Phishing Attack Using BlackPhish Tool – Complete Demo & Awareness
Phishing attacks are one of the most common threats in the digital world. To understand how they work, cybersecurity students and ethical hackers often explore tools like BlackPhish. In this blog, we’ll look at how BlackPhish is used to simulate a phishing attack, what steps are involved, and how to stay protected from such threats.
Disclaimer: This blog is for educational purposes only. Our aim is to spread awareness and help people protect themselves. Do not use these techniques for illegal activities.
 Watch Full Video Tutorial Here:
Watch Full Video Tutorial Here:
 What is BlackPhish?
What is BlackPhish?
BlackPhish is an open-source phishing tool created by @yangr0 that allows users to simulate phishing attacks on various platforms like Instagram, Facebook, Twitter, etc. It’s designed for educational demonstrations and red team testing.

https://github.com/yangr0/BlackPhish
 How to Use BlackPhish – Step-by-Step
How to Use BlackPhish – Step-by-Step
Let’s skip the theory and jump right into the practical part.
Step 1: Clone the Repository
git clone https://github.com/yangr0/BlackPhish
cd BlackPhish
bash BlackPhish.sh
This will launch the tool in your terminal.
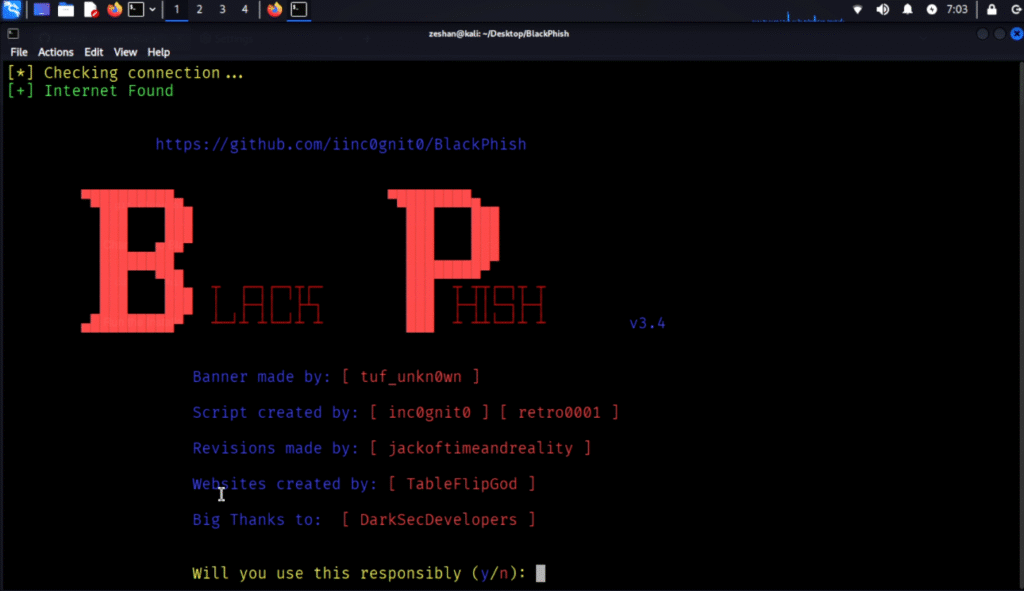
Step 2: Select Platform and Service
Once the tool is running:
You’ll see a menu with multiple platforms (e.g., Instagram, Facebook, Snapchat).
Select the platform you want to simulate phishing for.
Then choose the specific service, such as Login Page, Free Followers, etc.
Example: Instagram → Free Followers Page
Step 3: Get the Phishing Link
After selection, the tool will generate a phishing link.
Copy this link and share it with the target (for demo/educational purpose only).
When the target opens the link, they’ll see a fake login page.
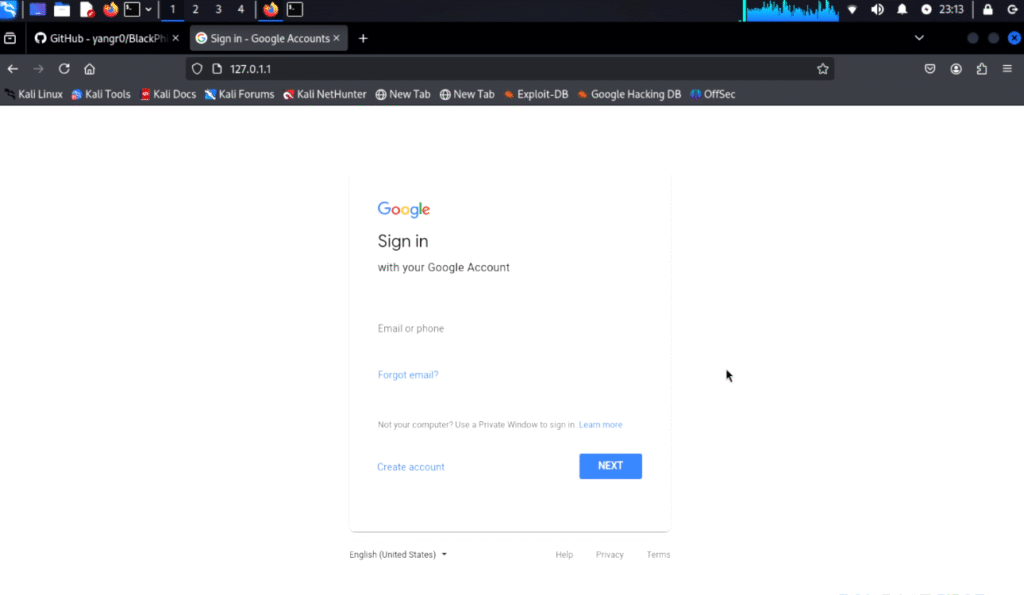
Step 4: Target Enters Credentials
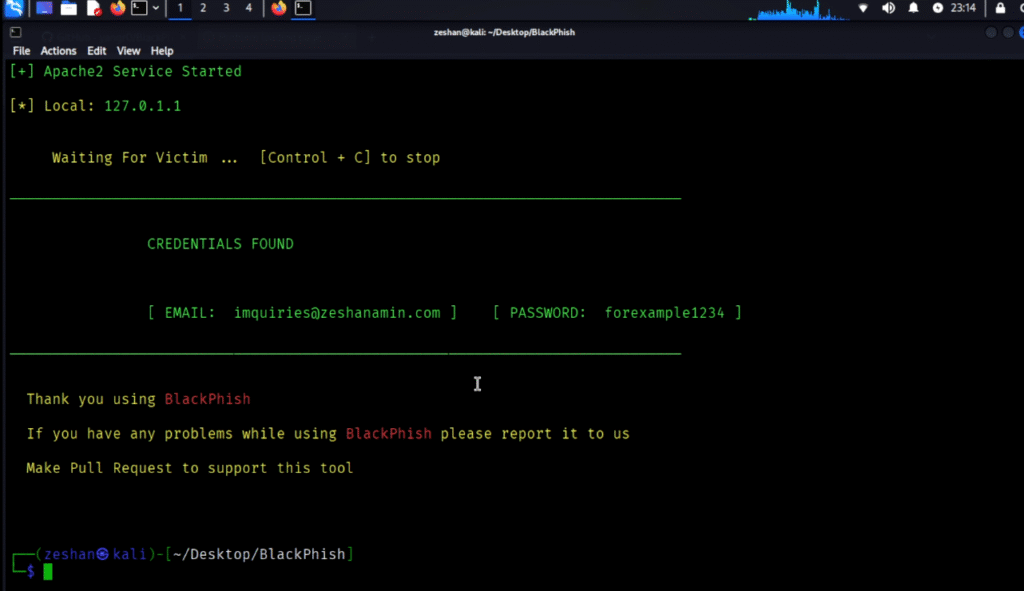
The target is tricked into entering their username and password.
On clicking “Login”, an error message appears on their screen.
Meanwhile, their credentials appear in your terminal in real-time.
 How to Stay Safe from Such Phishing Attacks
How to Stay Safe from Such Phishing Attacks
It’s very important to understand how phishing works so you can avoid falling for it. Here are a few tips to protect yourself:





 Final Thoughts
Final Thoughts
Tools like BlackPhish are widely used in ethical hacking labs and training programs to demonstrate phishing techniques. By understanding how attackers operate, we can build better defenses and educate others about cyber hygiene.
Again, this content is meant only for education and cybersecurity awareness. Never use these tools against anyone without permission.


