QR Phishing Attack using HiddenEye Tool – Ethical Hacking Demo
In the world of cybersecurity, attackers are constantly coming up with clever ways to trick users. One such method is QR phishing — where a fake QR code leads users to a malicious page. In this blog, we’ll explore how QR phishing works using a well-known tool called HiddenEye Legacy, purely for educational and awareness purposes.
Disclaimer: This article is strictly for educational purposes. The goal is to spread awareness about phishing attacks so you can recognize and prevent them. Never use these techniques for illegal or unethical purposes.
 Tool Used: HiddenEye Legacy
Tool Used: HiddenEye Legacy
GitHub: https://github.com/Morsmalleo/HiddenEye_Legacy
HiddenEye is a popular open-source phishing tool used by cybersecurity students and researchers to understand phishing tactics. In this case, we used it to simulate an Instagram QR phishing attack that pretended to offer free followers.
 How the QR Phishing Attack Works
How the QR Phishing Attack Works
Let’s break down the entire process step-by-step:
1. Cloning HiddenEye
git clone https://github.com/Morsmalleo/HiddenEye_Legacy
cd HiddenEye_Legacy
chmod +x HiddenEye.py
python3 HiddenEye.py
Make sure you have Python 3 and necessary dependencies installed.
2. Selecting Instagram Phishing Page
Once you launch the tool:
From the main menu, select
8for InstagramThen select
5for the Free Followers Page
This phishing page looks like a giveaway — users believe they’re getting free Instagram followers by logging in.
3. Skip Cloudflare & Login Settings
Skip any options that ask for Cloudflare or loading settings — just press Enter.
When asked for the port number, enter
5555or any available port.
4. Hosting the Page Locally or Globally
The tool will ask about redirect URL — leave it blank.
You can run it on
localhostor use ngrok for global access:
ngrok http 5555
This will give you a public link to the phishing page.
5. Turning the Link into a QR Code
To make the attack more convincing:
Use a free tool to convert the phishing link into a QR code
Example tool: https://www.qr-code-generator.com
6. Designing a Fake Promo Poster
Use Canva to create a professional poster.
Add the QR code and a heading like:
“On our 8th Anniversary, we’re giving away FREE followers. Just scan & claim!”
Print the poster or share it digitally.

7. Victim Interaction
When someone scans the QR:
It opens the phishing page mimicking Instagram.
They enter their username and password, believing it’s legit.
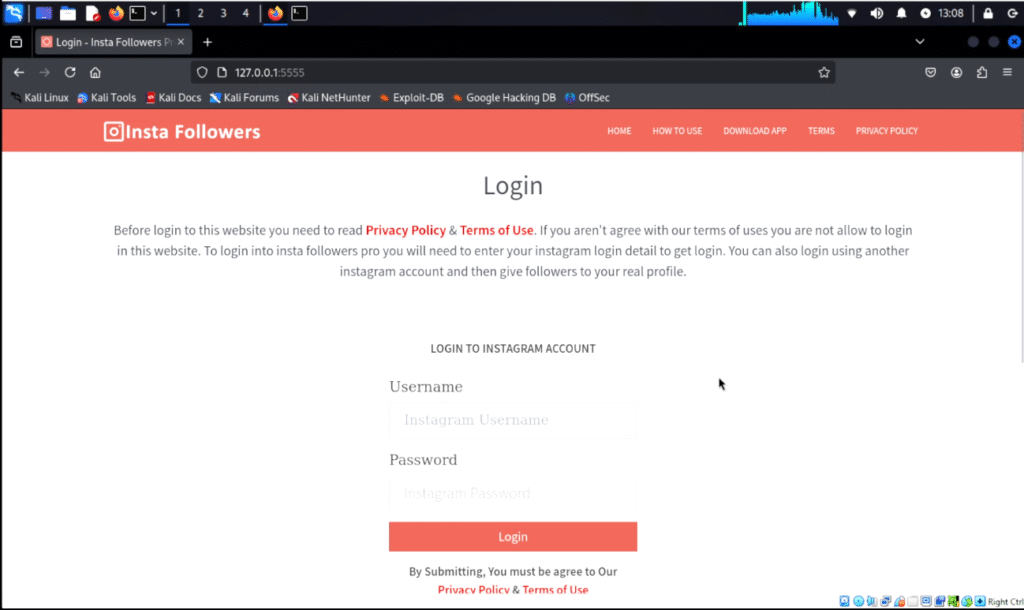
Upon clicking “login”, they get an error page.
Meanwhile, the attacker receives the credentials in the terminal.
 How to Protect Yourself from QR Phishing
How to Protect Yourself from QR Phishing
Cybercriminals are exploiting QR codes because people trust them blindly. Here’s how you can stay safe:
- Never scan unknown QR codes from posters or public places.
- Verify the URL that opens after scanning — check if it’s official.
- Use two-factor authentication (2FA) for all social accounts.
- Educate yourself about social engineering and phishing traps.
- Install security apps that warn you about phishing pages.
Final Thoughts
QR phishing is a real threat and is becoming more common with time. This blog was created only for ethical hacking education, so you can understand how these attacks work and how to defend yourself. Always think twice before scanning a code or entering credentials on unfamiliar sites.

